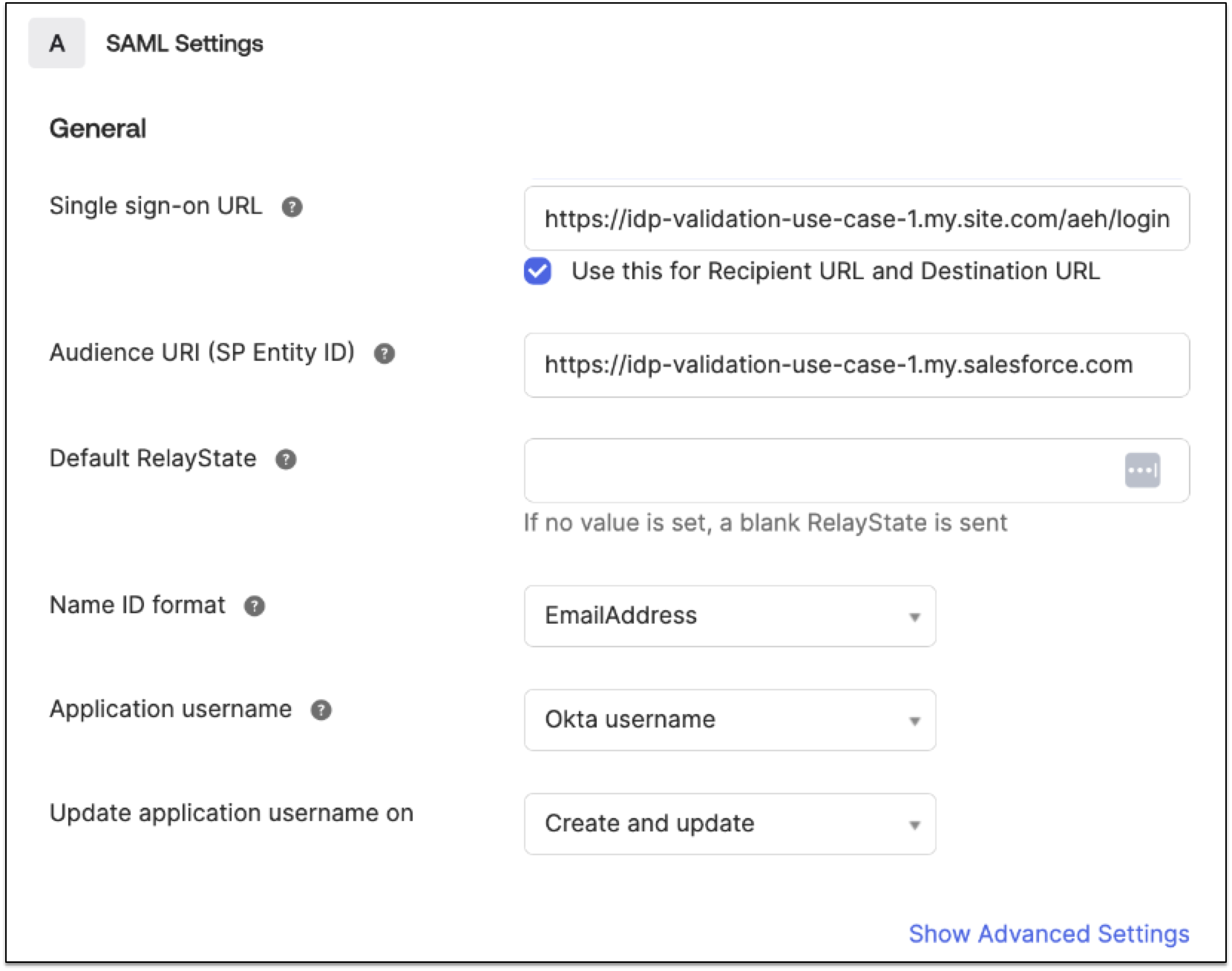
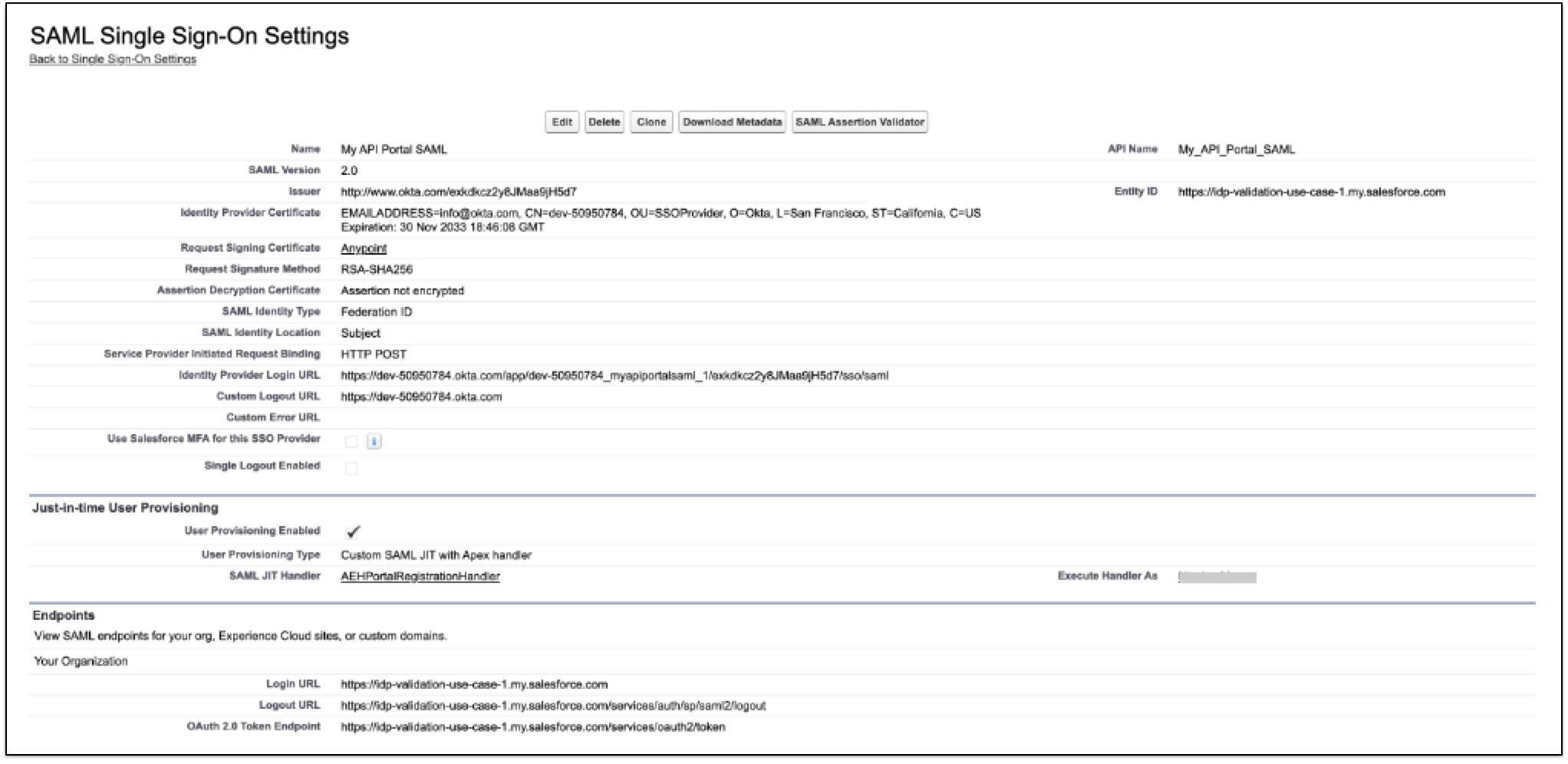
Create a new application for the API Experience Hub portal in the identity provider using OpenID Connect.
-
In Okta, create an OpenID Connect Web application. For more information, see Create OIDC app integrations.
-
From the General Settings section, complete the following fields:
Field Value App integration name
Enter a name for the app.
Grant type
Select Authorization Code.
Assignments
Select Limit access to selected groups.
Selected group(s)
Enter the name of the group who must have access to the application.
-
Verify that your identity provider sends the expected claims listed in the Before You Begin section.
-
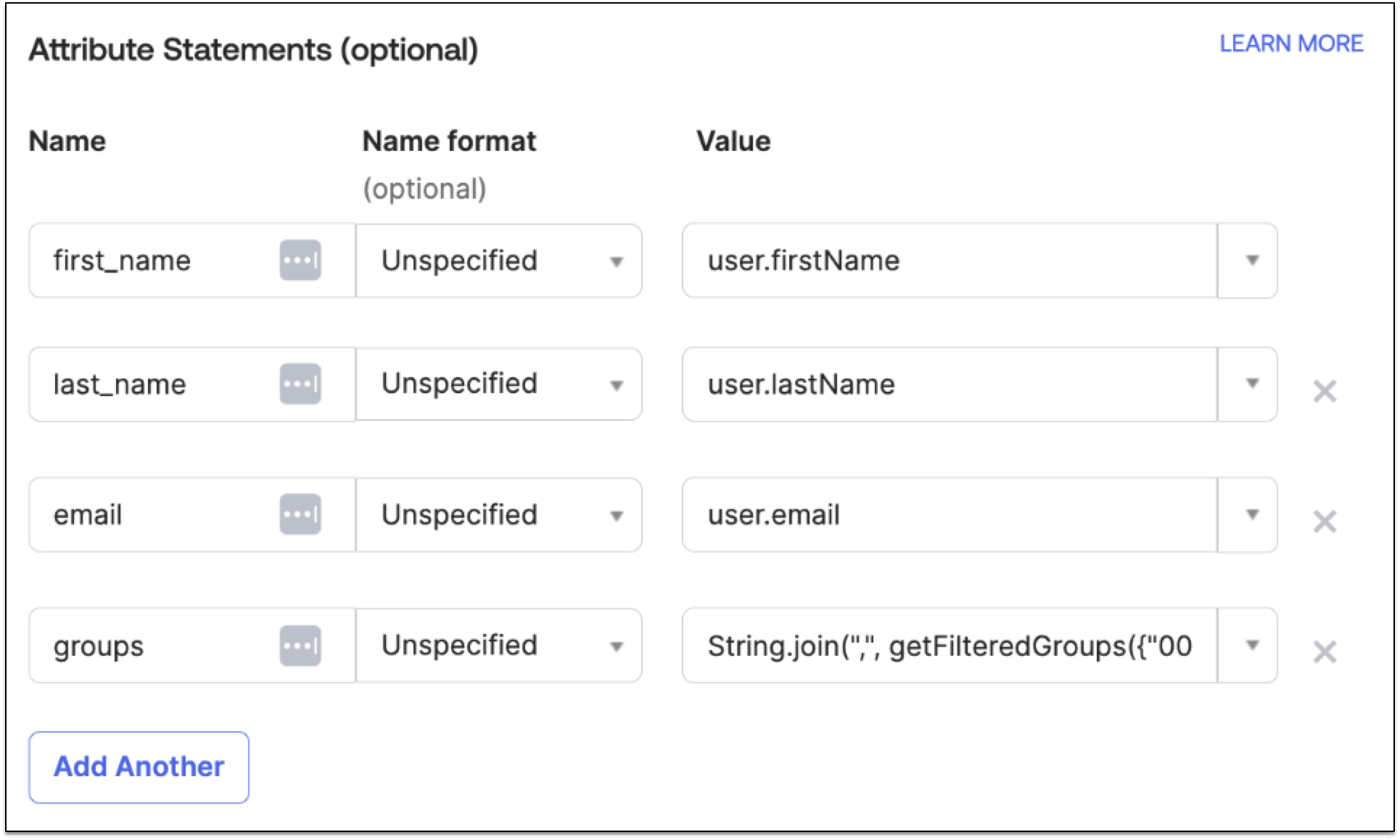
Configure the claims that the application sends.
For example, for OpenID Connect for Okta, configure the groups claim using the following steps:
-
From the Sign On tab, click Edit from the OpenID Connect ID Token section.
-
From Groups claim type, select Filter.
-
From Groups claim filter, enter
groups. -
Select Matches regex for the expression then enter
.*for wildcard.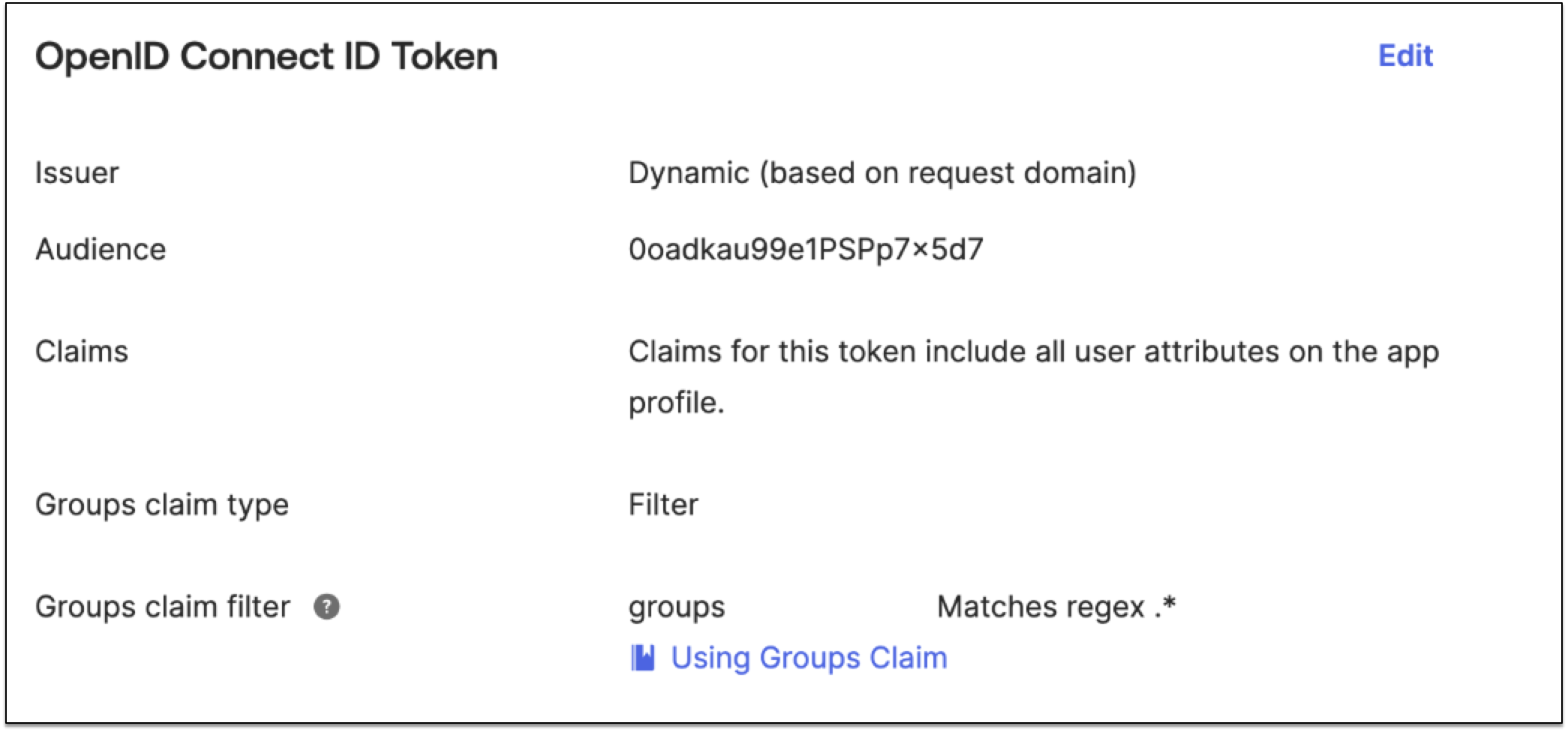
-
-
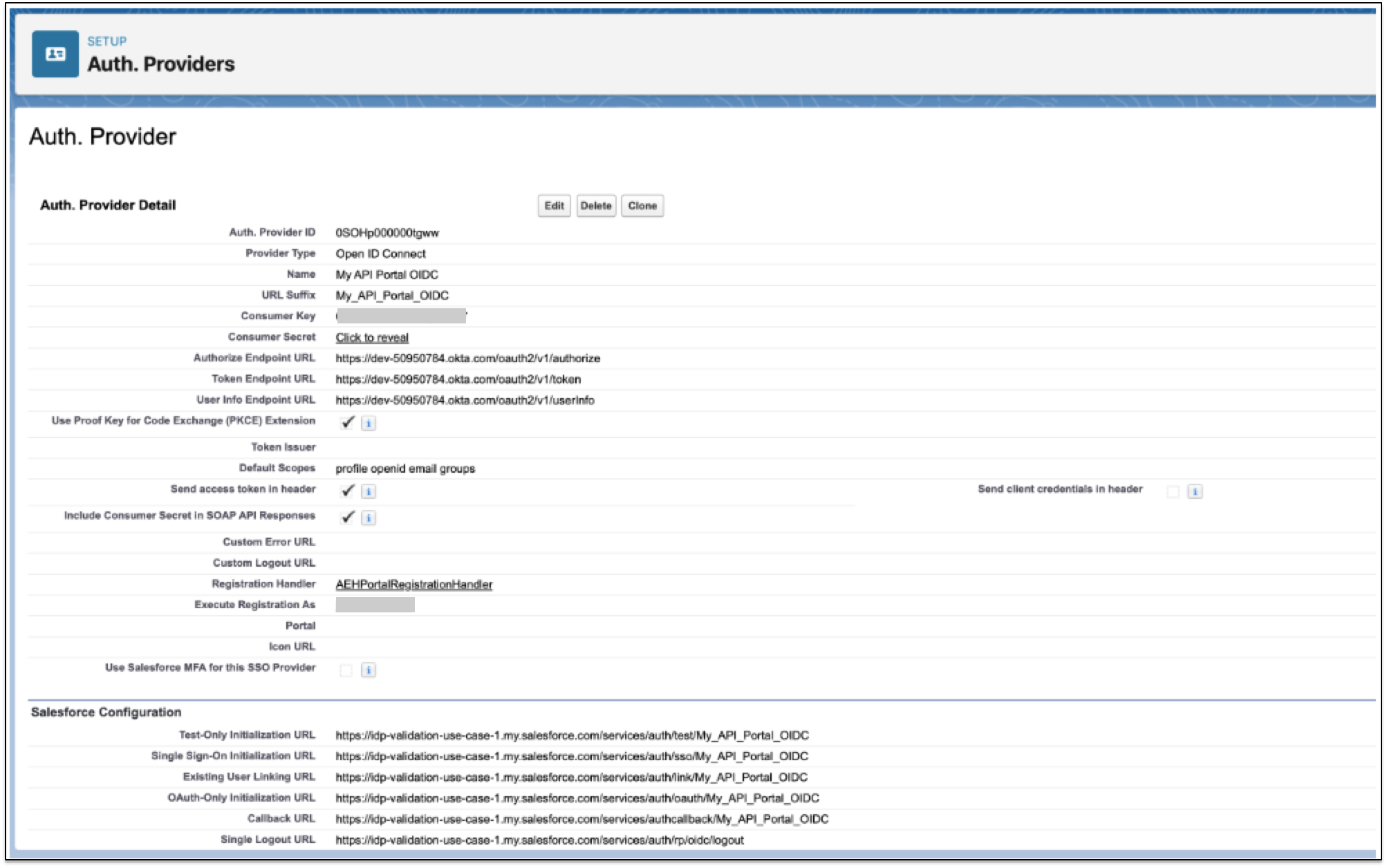
Configure an authentication provider for Salesforce using OpenID Connect.
You set up the auth provider or SSO settings in Salesforce with the identity provider application information.
-
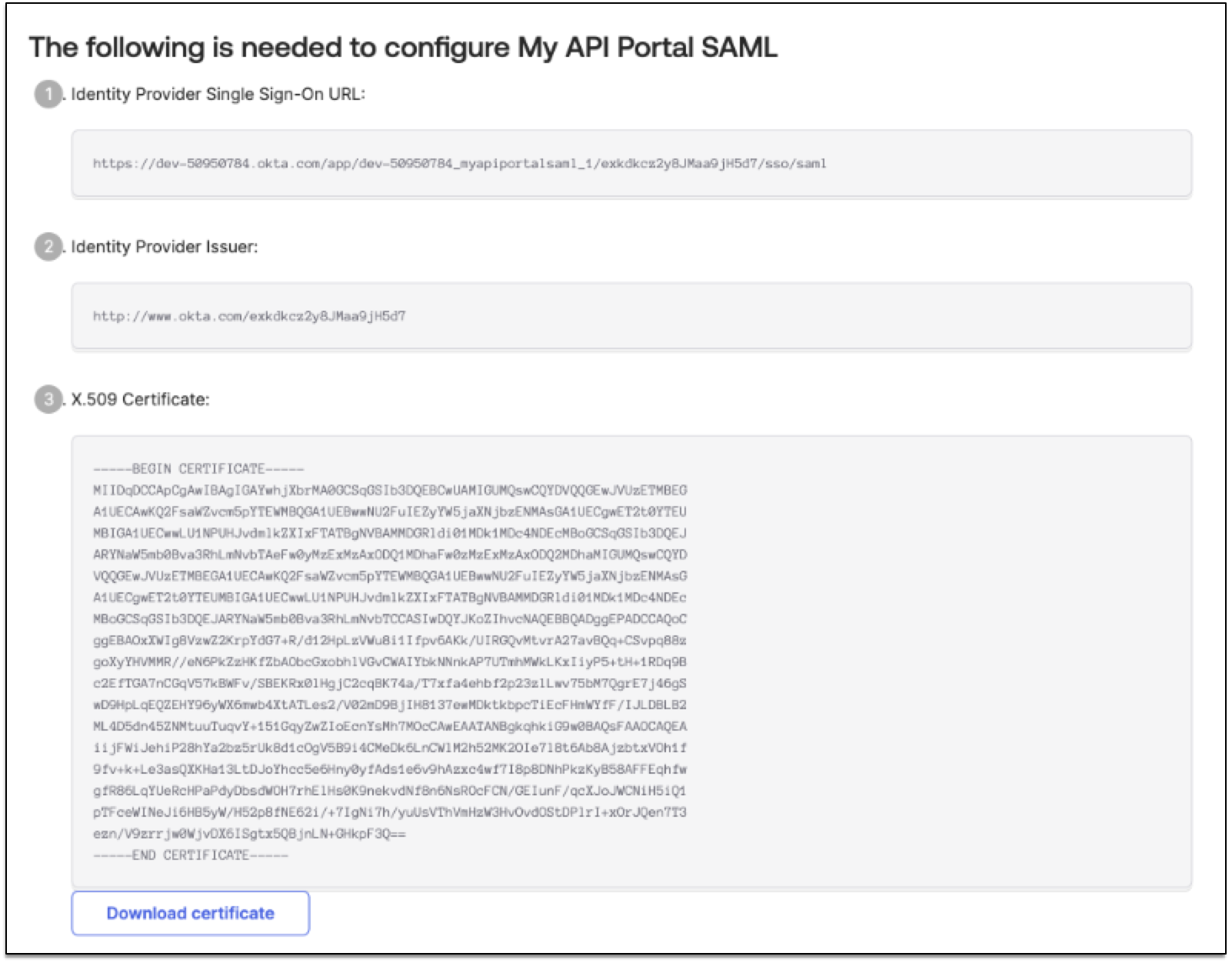
From the OpenID Connect application, get these configuration values:
-
Client ID
-
Client Secret
-
Authorize Endpoint URL
-
Token Endpoint URL
-
User Info Endpoint URL
-
-
In Salesforce, go to Setup.
-
In the Quick Find box, enter
Auth, and then select Auth. Providers. -
Click New.
-
For Provider Type, select OpenID Connect.
-
Complete the following fields:
Field Value Provider Type
OpenID Connect
Name
Enter a name for the provider.
Consumer Key
Enter the client ID from the identity provider.
Consumer Secret
Enter the client secret from the identity provider.
Authorize Endpoint URL
Token Endpoint URL
User Info Endpoint URL
Default Scopes
profile openid email groups
Registration handler
AEHPortalRegistrationHandler
Execute Registration As
Select an administrator user.
-
Click Save.
-
-
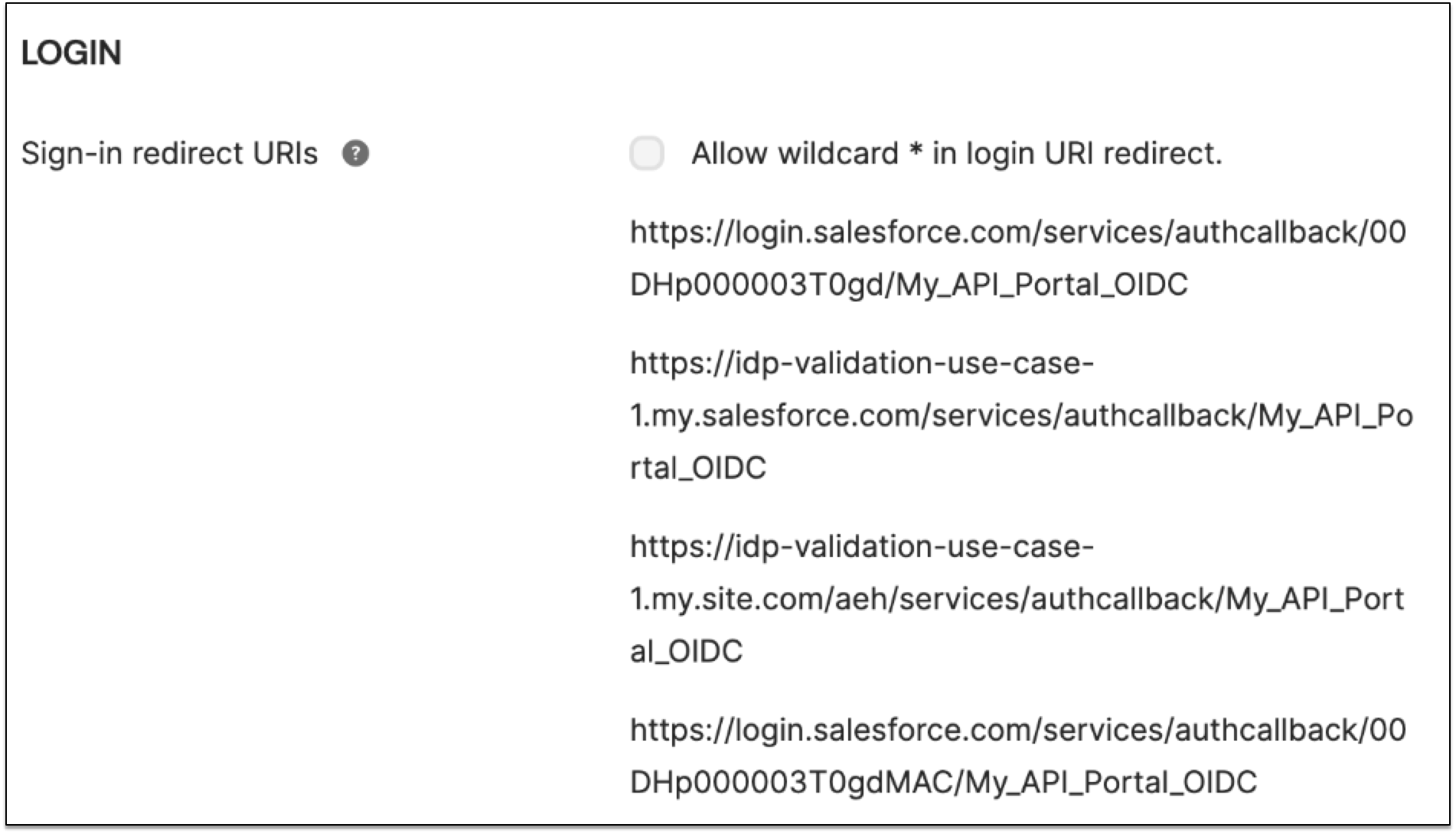
Configure the redirect URIs for the portal.
To configure the redirects, use your 15 digit organization ID and 18 digits org ID and add a URL for each organization ID.
-
In the Okta application, select the General tab. Add the following URLs for Sign-in redirect URIs:
-
https://${domain}.my.site.com/aeh/services/authcallback/${authProviderURLSuffix}
To find the URLs:
-
For salesforceOrganizationId, go to Setup > Company Information.
-
For authProviderURLSuffix, go to Setup > Auth Providers, click your auth provider, and select URL Suffix.
-
For domain, go to Setup >* My Domain* > Current My Domain URL.
-