To Configure and Apply an OAuth 2.0 Token Validation Policy
You can configure access scopes if you use any one of the OAuth 2.0 policies provided in API Manager. You specify the scope of access that client applications have using their credentials. The provider (OpenAM, OpenID Connect, PingFederate, or Mule provider) has to support the scopes you define for the application. You need to know the names of the scopes as defined in OpenAM, PingFederate, or Mule provider or the OpenID Connect Token Introspection endpoint, and enter them in string format when you configure and apply the policy on Anypoint Platform. Scope names are case-sensitive.
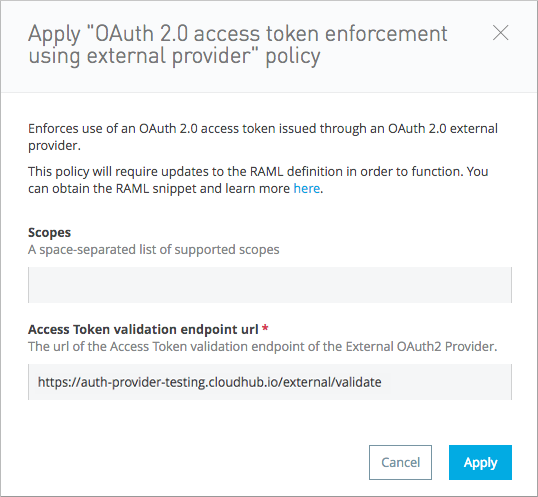
To apply the policy to an API, use the general procedure for applying policies. Configure the optional scopes and required token validation endpoint URL as described in this procedure.
Scopes
-
In the optional Scopes field, enter a space-separated list of supported OAuth scopes, such as
read write. The scopes are case-sensitive.
-
Specify scopes that match one or more of the scopes defined on the referenced OAuth 2.0 Provider application.
In the case of a Mule OAuth 2.0 provider, if the Mule provider does not define scopes, leave this field blank. If you plan to use API Console to simulate the API, leave scopes blank and apply the CORS policy.
Access Token Validation Endpoint URL
AAuth 2.0 Access Token Enforcement Using External Provider policy requires the Access Token validation endpoint url, which defines the service that will be called to validate the access token.
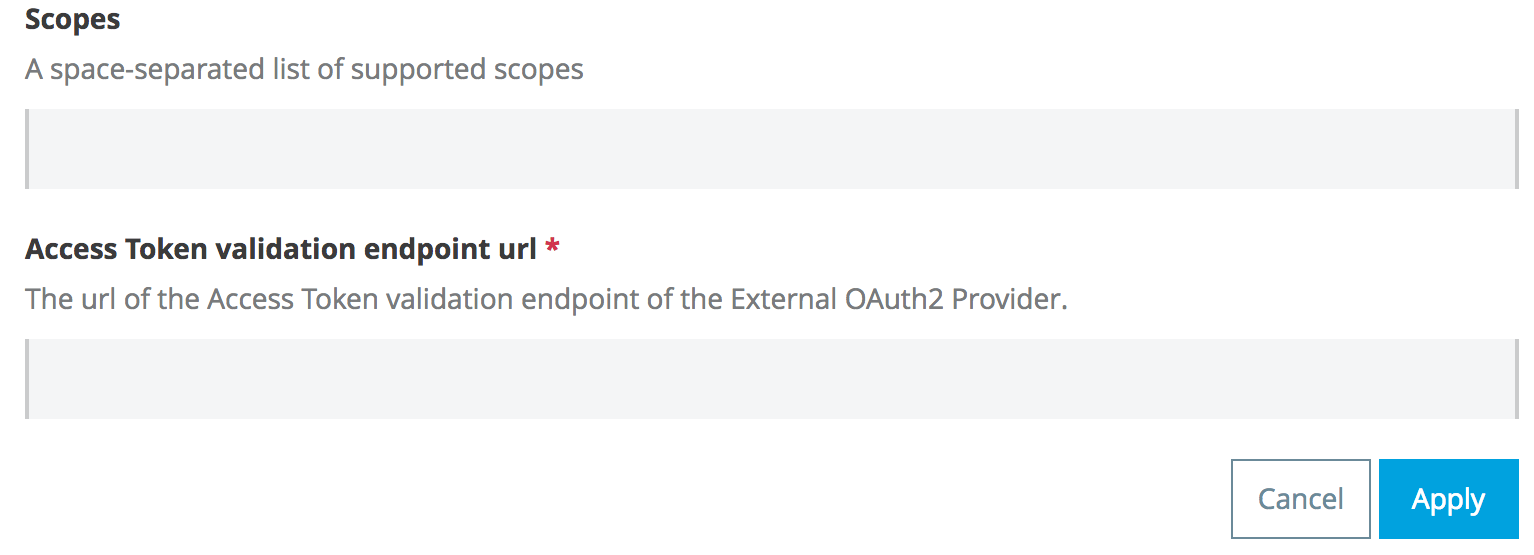
In the required Access Token validation endpoint url field, you enter the URL of the external OAuth 2.0 Provider used for granting the access token, for example https://oauth2provider.cloudhub.io/validate.