Configuring JCE Cryptography
The Java Cryptography Extension (JCE) strategy lets you use Java’s powerful encryption features. You have the flexibility to encrypt an entire message or just specific parts of it using either of these two methods:
-
Password-based encryption (PBE)
This method enables you to encrypt and sign content by simply providing an encryption password. -
Key-based encryption (KBE)
Similar to PGP and XML encryption, this method enables you to configure a symmetric or asymmetric key to perform encryption and signing operations.
Use the Cryptography Module JCE operations to configure these methods.
| If you’re upgrading to Cryptography Module 2.1, configure the required Java dependencies so your project compiles. For details, refer to Upgrading and Migrating Cryptography Module 2.x. |
Before You Begin
You are familiar with PBE and KBE encryption, concepts of public and private keys, and asymmetric cryptography.
Configure PBE Encryption
This method takes your password and runs it through a hash function to create a symmetric encryption key. This generated key works with standard encryption algorithms. Because PBE only needs a password, you don’t need a separate Global Configuration Element for JCE PBE operations.
Configure JCE PBE Operations in Anypoint Studio
Follow these steps:
-
In Anypoint Studio, drag a Cryptography Module JCE PBE operation to the canvas flow.

-
In the operation configuration window, set the Algorithm, Password Password salt and Iteration count properties: +git s image::crypto-jce-setting.png["Configuration settings for JCE encrypt PBE with algorithm, password, password salt, iteration options"]
XML Examples
These are XML examples for each of the JCE PBE operations:
-
Jce encryption pbe
<crypto:jce-encrypt-pbe password="a-Sup3r_Secure-Passw0rd"/>If you don’t specify an algorithm, the module uses
PBEWithHmacSHA256AndAES_128. -
Jce decrypt pbe
<crypto:jce-decrypt-pbe algorithm="PBEWithHmacSHA256AndAES_128" password="a-Sup3r_Secure-Passw0rd"/> -
Jce sign pbe
<crypto:jce-sign-pbe password="a-Sup3r_Secure-Passw0rd"/>If you don’t specify an algorithm, the module uses
PBEWithHmacSHA256. -
Jce validate pbe
<crypto:jce-validate-pbe password="a-Sup3r_Secure-Passw0rd" algorithm="PBEWithHmacSHA256" expected="#[vars.expectedSignature]"/>The
expectedparameter defines the signature used to validate the message.
Configure KBE Encryption
Configure a symmetric or asymmetric key to perform encryption and signing operations.
Configure JCE KBE Operations in Anypoint Studio
Follow these steps:
-
In Anypoint Studio, drag a Cryptography Module JCE KBE operation to the canvas flow.
-
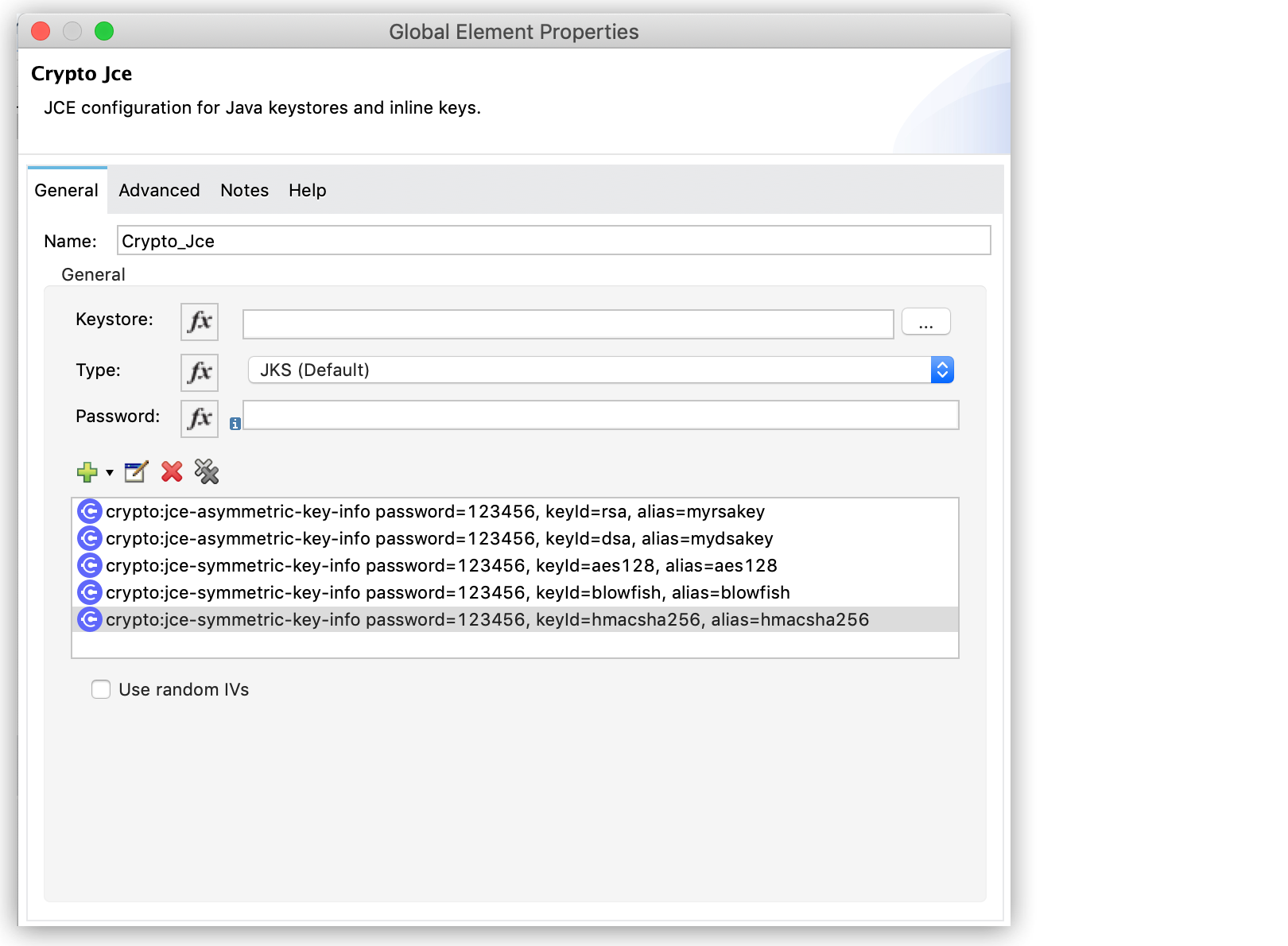
In the operation configuration window, select an existing Module configuration, or create a new one by configuring the Keystore, Type (JKS, JCEKS, PKCS12), and Password parameters.
You can also add symmetric or asymmetric key information to use in sign operations:
-
Configure Key selection by using a Key id value previously defined in the module configuration, or define a new one for this operation:
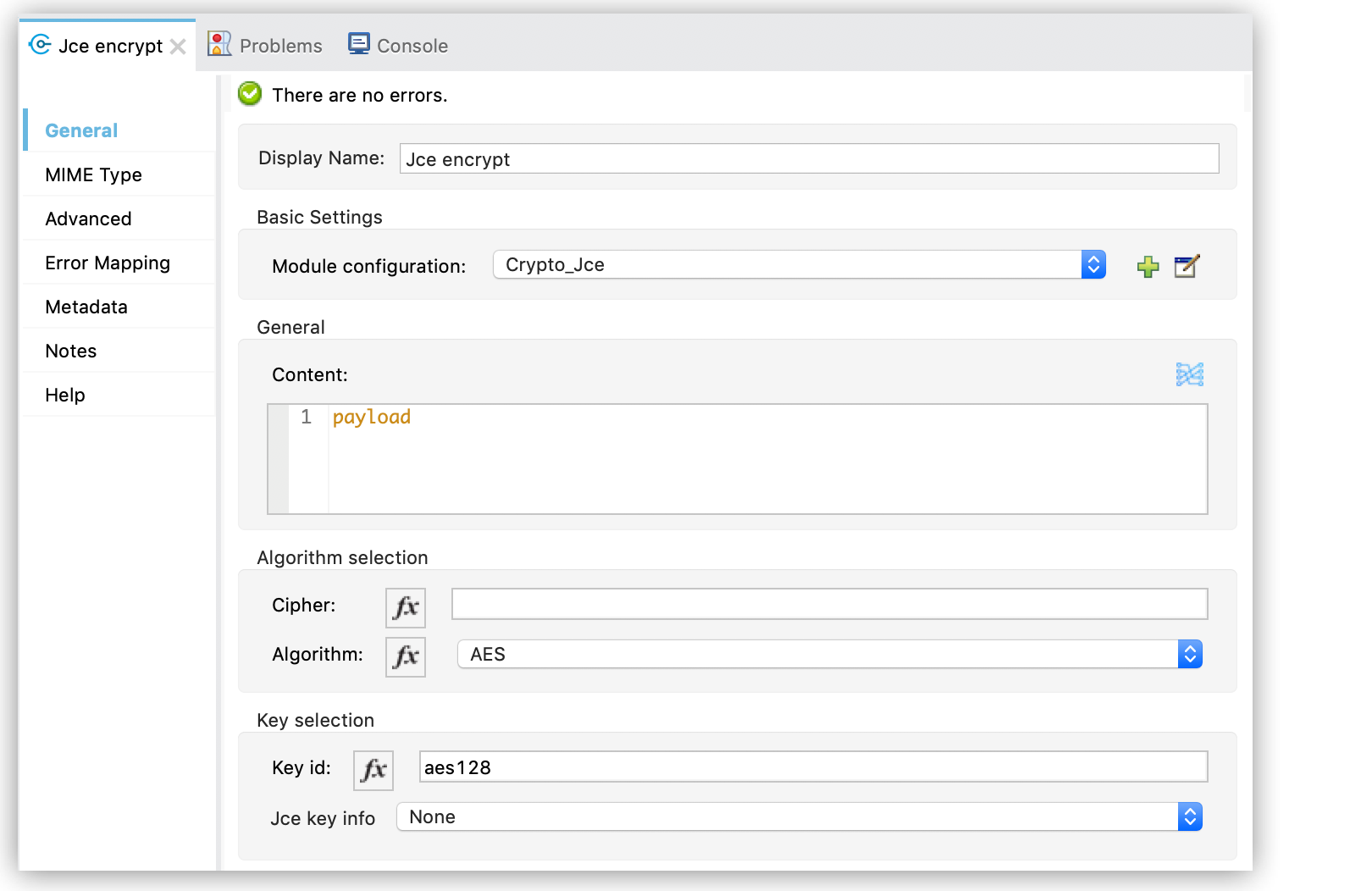
-
Select the algorithm to use during the operation.
XML Examples
These XML examples show a JCE configuration that defines symmetric and asymmetric keys and different operations using these keys.
-
Configuration
In this example, the JCE configuration contains a keystore with different types of keys:
<crypto:jce-config name="jceConfig" keystore="jce/keys.jceks" password="123456" type="JCEKS"> <crypto:jce-key-infos> <crypto:jce-symmetric-key-info keyId="aes128" alias="aes128" password="123456"/> <crypto:jce-symmetric-key-info keyId="blowfish" alias="blowfish" password="123456"/> <crypto:jce-symmetric-key-info keyId="hmacsha256" alias="hmacsha256" password="123456"/> <crypto:jce-asymmetric-key-info keyId="rsa" alias="myrsakey" password="123456"/> <crypto:jce-asymmetric-key-info keyId="dsa" alias="mydsakey" password="123456"/> </crypto:jce-key-infos> </crypto:jce-config> -
Asymmetric Encryption
In this example, the operations Jce encrypt and Jce decrypt use the asymmetric keys defined in the previous configuration.
Encrypting a Message<crypto:jce-encrypt config-ref="jceConfig" keyId="rsa" algorithm="RSA"/>Decrypting a Message<crypto:jce-decrypt config-ref="jceConfig" keyId="rsa" algorithm="RSA"/> -
Symmetric Encryption
In this example, the operations Jce encrypt and Jce decrypt use the symmetric keys defined in the previous configuration.
Encrypting a Message<crypto:jce-encrypt config-ref="jceConfig" keyId="aes128" algorithm="AES"/>Decrypting a Message<crypto:jce-decrypt config-ref="jceConfig" keyId="aes128" algorithm="AES"/> -
Signature and Validation
In this example, the Jce sign and Jce validate operations use a key defined in the previous configuration:
Signing a Message<crypto:jce-sign config-ref="jceConfig" keyId="dsa" algorithm="SHA256withDSA"/>Validating a Signature<crypto:jce-validate config-ref="jceConfig" keyId="dsa" algorithm="SHA256withDSA" expected="#[vars.expectedSignature]"/>The
expectedparameter defines the signature used to validate the message.



