KexAlgorithms ecdh-sha2-nistp521,ecdh-sha2-nistp384,ecdh-sha2-nistp256,diffie-hellman-group18-sha512,diffie-hellman-group17-sha512,diffie-hellman-group16-sha512,diffie-hellman-group14-sha256
Ciphers aes128-cbc,aes128-ctr,aes192-cbc,aes192-ctr,aes256-cbc,aes256-ctr
HostKeyAlgorithms ssh-rsa,rsa-sha2-256,rsa-sha2-512
MACs hmac-sha1,hmac-sha2-256,hmac-sha2-512Configure Security Parameters of SSH Connection
The following example shows how to configure the Anypoint Connector for SFTP (SFTP Connector) to override security parameters using Anypoint Studio.
Create a Configuration Override File
Follow these steps to create the file:
-
Navigate to your
src/main/resourcesfolder. -
Create a config file, for example,
mule_sshd_configwith the following SSHD content. The file follows the format of ansshd_configfile: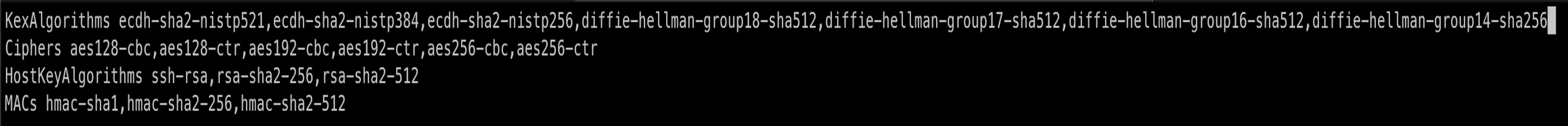
-
Configure the keys and values accordingly. If you do not provide a key, then default values are used.
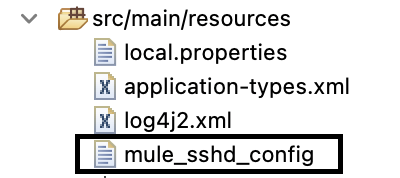
The following example shows the location of the config file within the src/main/resources folder:
Configure the Override File in Anypoint Studio
Follow these steps to configure the override file:
-
In Studio, navigate to the Global Elements tab.
-
In the Choose Global Type window, type
sftpin the search bar. -
Select SFTP Config.
-
Click OK.
-
Go to the Advanced tab.
-
Under Security Configuration, enter
ssh config override file. -
Enter the path to the file, for example:
${app.home}/mule_sshd_config. -
Complete the remaining connection fields.
-
Click Test Connection….
-
Click OK.
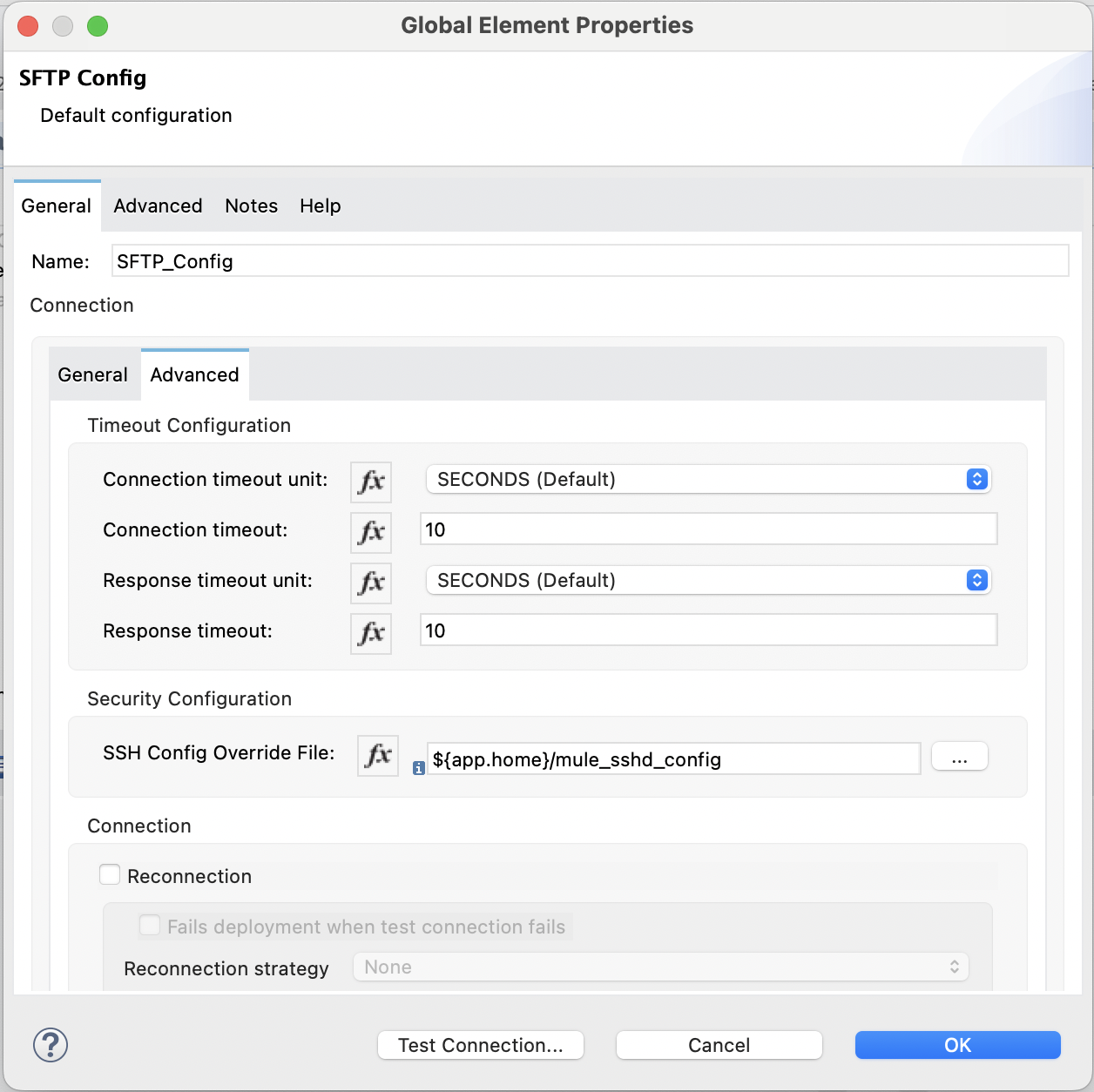
In the Configuration XML editor window, the configuration looks like this:
<sftp:config name="SFTP_Config" doc:name="SFTP Config" >
<sftp:connection host="localhost" sshConfigOverride="${app.home}/mule_sshd_config">
</sftp:connection>
</sftp:config>Verify the Override File Creation
Consider the following points when verifying the file creation:
-
Search for the log
Read the config fileand verify that the filename and the configuration values fetched from the file are valid. -
Find ignored configs with the log line
Config keys found but ignored. -
Check that if the connector is unable to locate the file, then it logs
Couldn’t locate config file.



